LXR Cloud provides cost-effective alternatives for API Gateway and API Management solutions.
Open-Source versions of Nginx & Kong & are packaged with LXR tools for OAuth/JWT, DevPortal, and resuable deployment patterns.
LXR iSign
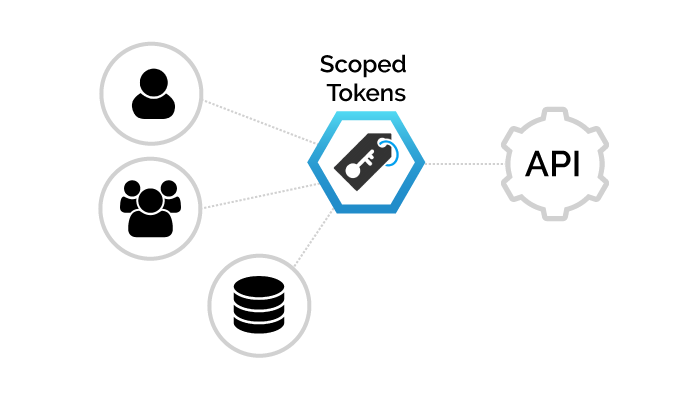
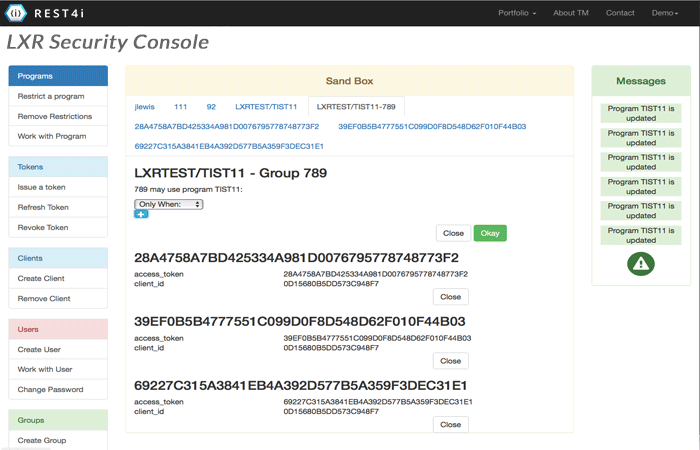
OAuth/JWT Management & Authentication
Instantly add scoped authentication, authorisation, and user management to secure your web or mobile apps
LXR iSign is a complete system for companies not implementing a full API Gateway, but who still need to add secure authentication, authorisation, and user management to apps and APi’s.
Learn More LXR Patterns
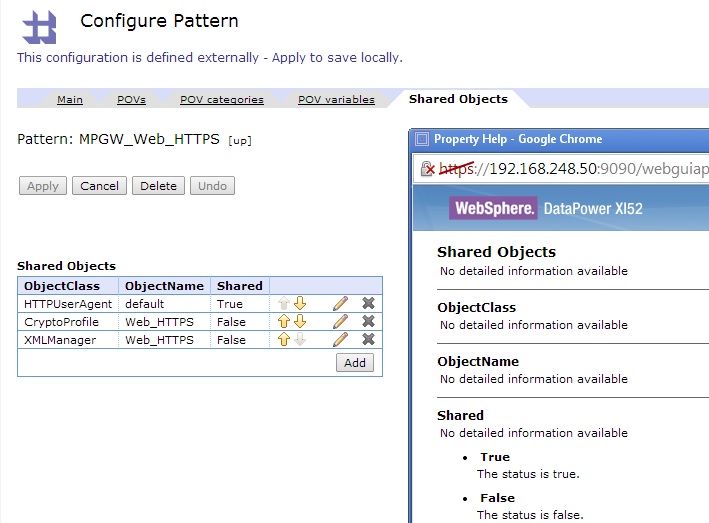
ReUsable Infrastructure Patterns
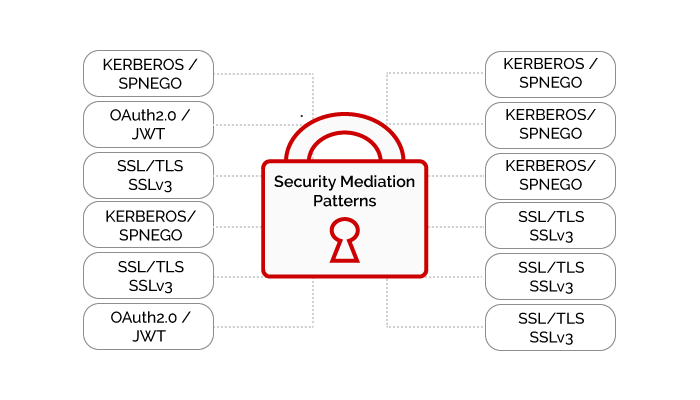
Improve Security & Save Deployment Costs with ReUsable Infrastructure Patterns for API Deployment
LXR Patterns are a set of pre-defined security mediation and infrastructure patterns. Used for common digital integration scenarios such as OpenBanking, PSD2, Industry 4.0, Acord etc.
Learn MoreLXR iScan
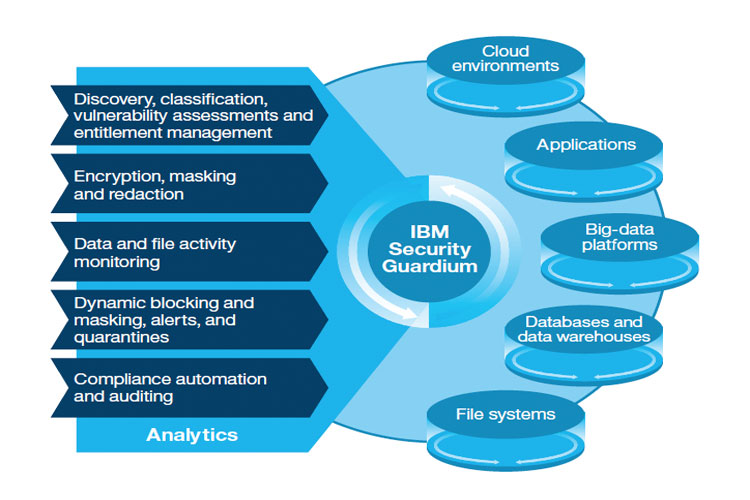
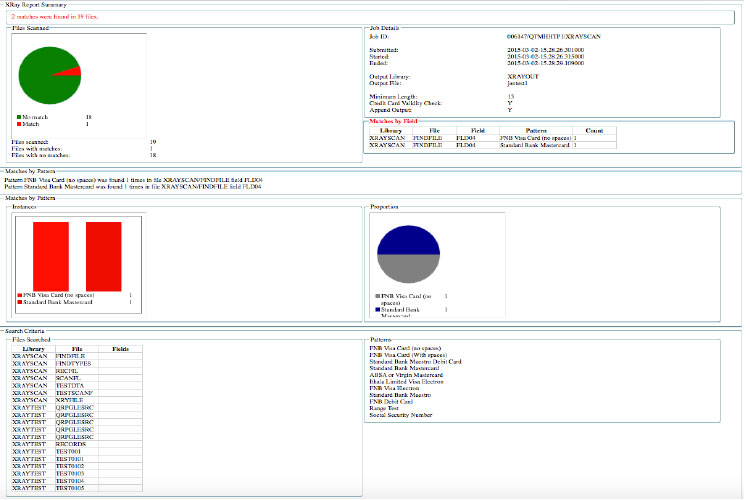
Scan for Sensitive Data on IBM i

LXR iScan helps secure the data that powers your business by uncovering exactly where it is, before anyone else does
LXR iScan is a data-pattern discovery tool for IBMi databases and IFS folders. LXR iScan scans storage media for credit card numbers or other sensitive data covered by regulatory compliance audits.
Learn More